A Guide to Project Management Fundamentals
WIP! But don't let that stop you from giving it a read! :D
This is a helpful guide to introduce you to project management, and the elements that make up a successful project.

WIP! But don't let that stop you from giving it a read! :D
This is a helpful guide to introduce you to project management, and the elements that make up a successful project.

This week, I came across a leadership framework that I couldn't resist sharing called Transformational Leadership by James V. Downton and James MacGregor Burns. Instead of honing in on the mistakes, missed deadlines, or gaps in skills, what if we led like our team is already winning?

So, what’s the deal with space and cyber security?

On December 2024, I had my keyless car stolen from my house. Understandably, I was distraught. I spent many months pondering how it could have happened and what made my car the ideal victim? After some research, and actually coming into possession of the vehicle after four months of it being lost in the abyss, I was able to piece together the puzzle. In this post, I hope to bring awareness to the security of modern vehicles, attacks that are actively being exploited, and ways a driver can protect their car from such exploits.

Arnavv Singh’s journey into cyber security began with a spark of curiosity in Year 12. While researching potential career paths, cyber security “immediately caught my attention" due to his strong interest in new tech. Currently studying a double degree in Bachelor of Cyber Security and Bachelor of Criminology at Deakin University, Arnavv is about to enter his final year. He hopes to eventually transition into a digital forensics or cyber investigation role.

Bree is a proactive third-year Bachelor of Cyber Security student at Deakin University passionate about ethical hacking, penetration testing, and cybersecurity awareness. She enjoys translating complex cybersecurity concepts into clear, actionable guidance for non-technical teams and founders, helping to bridge the gap between technical expertise and real-world business protection.

"We can't let good be just a word. It has to mean something." - Elphaba
This weekend, I indulged in the new installment of the Wicked series, Wicked 2: For Good. Traditionally, I would have raved about how much I enjoyed it, but the messaging within the film echoed something that I observe in cyber security.
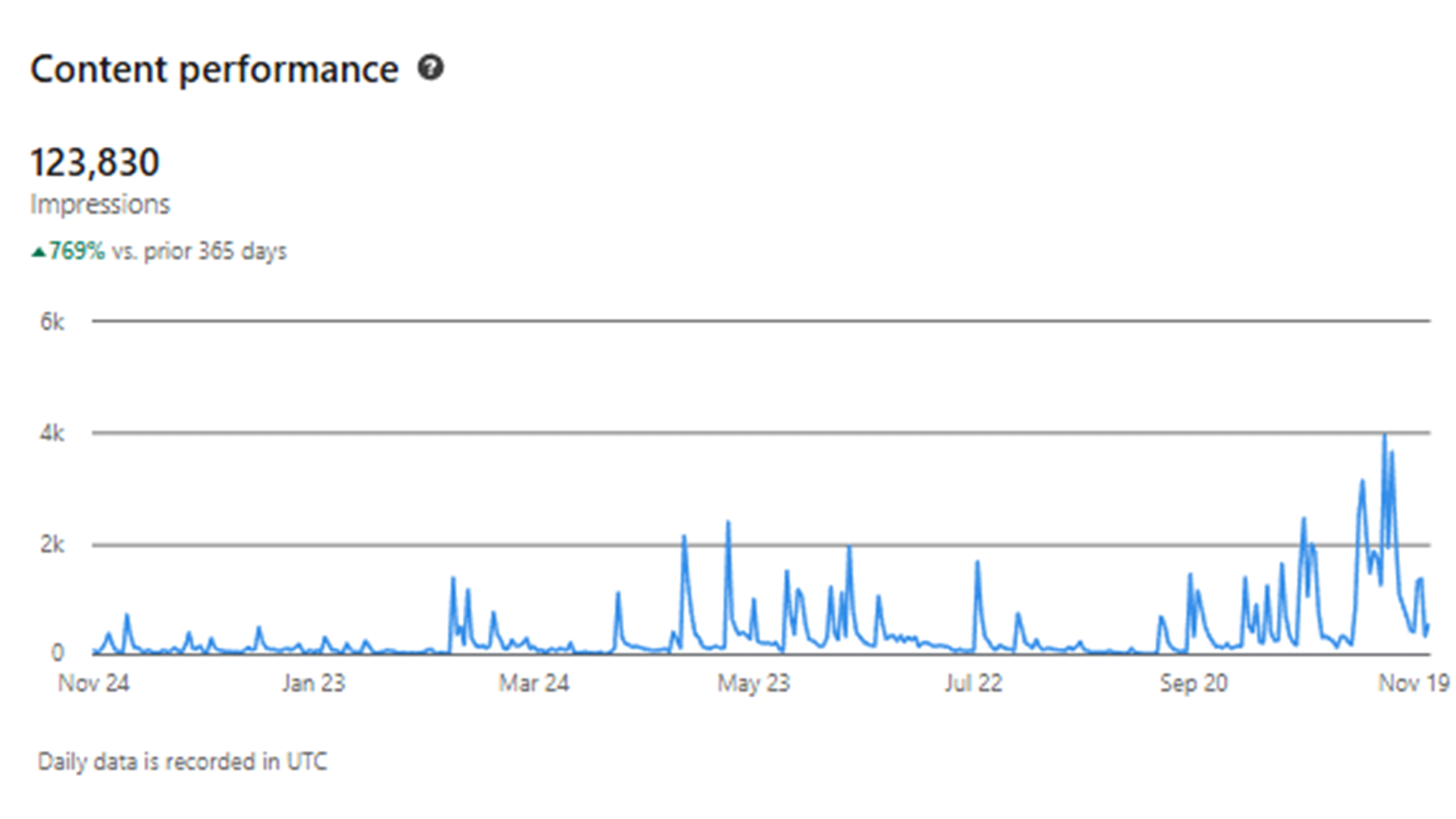
Gain access to a proven content strategy that I actually used as a social media manager that can help you get started with writing blog posts!

Threat actors have shifted their focus from large-scale ransomware attacks to more subtle and persistent threats. One that you may have seen on news sites or on LinkedIn are infostealers. This post dicusses hwo these malicious programs are designed to discreetly harvest sensitive data from an infected system.

Completed a cybersecurity simulation with Datacom, undertaking a risk assessment to identify threats pertaining to APT34, otherwise known as Helix Kitten.